Customize your financial management process to fit in exactly the way you wish to operate using Conversational AI.
Best Cybersecurity Company in USA
Blockchain Cybersecurity Service
-
Cryptokey and Genesis block tampering
-
Protection from malicious code
-
Good Business Consultants are Willing to Travel Where the Work Is
-
Permissions escalation
-
Misused timestamps
-
Inappropriate consensus mechanism
-
Lack of security controls and DDoS attacks
-
Poor integrity of Blockchain models
-
Packet sniffing & MITM attacks
How NidiTech helps you shield against Blockchain?
Security Design
Reduce security concerns while increasing scalability.
Technology Audit
Examine Blockchain technology and procedures.
Compliance Audit
Check regulatory compliance of PII and other critical data.
Security Assessment
Avert compromise, manipulation, and tampering of the ecosystem.
Managed Detection and Response (MDR) Services
End to End Managed services will offer our AI and ML platform, it will continuously collects data, analyzes it and correlates threat data for identify threads to protect clients IT assets

Our services in the area include:
Data collection and proactive thread identification.
24*7 monitoring and Provide Insights about vulnerabilities.
Discover security flaws in Endpoints, user behaviours.
Investigating and Managing breaches to protect
Cloud cybersecurity service
Our Cloud CyberSecurity Services offering provides a holistic approach to cloud security, effectively protecting data and applications, cloud system apps while ensuring regulatory requirements are met and business goals are not compromised on.
Our services in the area include:
Cloud assets and network topology end to end visualisation.
Cloud data protection and active defense mechanism.
Advanced identity and access management (IAM).
Implementing best practices and Proactive security risks.
Endpoint Detection and Response (EDR) Service
We actively monitor unknown endpoint threats and respond immediately (Endpoint Detection and Response). We analyze the threats and once a threat is validated, we contain the compromised endpoints and take prompt action to protect against similar attacks in future.

Our services in the area include:
Monitor and collect activity data from endpoints.
Deep Analytics on data to identify threat patterns
Automatically respond to identified threats to remove.
Using Forensics and analysis tools to research.

Advanced Threat Protection (ATP) Service
Advanced threat protection (ATP) security solutions that defend against highly sophisticated malware or targeted hacking-based attacks especially targeting sensitive data hence we go beyond traditional point-in-time detection and offer innovative advanced threat protection services that promptly identify attacks in realtime and alert client organizations, enabling quick mitigation against vulnerabilities.
Our services in the area include:
Cloud based AI and ML system to monitor threat assessments, detection on malwares
Red team services continuously detect, stimulate and and counter threats.
Pentesting and remediation on applications, cloud infrastructures.
Source code reviews and remediations on regular intervals for protect
IoT Cybersecurity Service
We offer complete end to end security services for IoT platform to protect IoT devices from cyber-attacks, reducing endpoint complexity and securing its integration with CRPP.

Our services in the area include:
IoT threat detection for Network traffic analysis, IoT device profiling and pattern detection
IoT Security solution Design, Implementation and Operation Management services
Source code reviews and remediations on regular intervals Strong convergence on IT

Advanced Network Security Management Services
Experts at our SOC help clients leverage the latest technologies to ensure robust network security.
Our services in the area include:
Readiness Assessment to analyse infrastructure landscape for network security
Right Technology selection based on security, compliance and overall business needs
Solution deployment and Security optimisation based on technology and business integrations
Overall network security management based on network health and security needs
Vulnerability Disclosure Service
Our vulnerability disclosure program offers a secure channel for researchers to report security issues and vulnerabilities, and typically includes a framework for intake, triage, and workflows for remediation.

Our services in the area include:
Vulnerabilities assessments on websites, networks, mobile apps and API endpoints
Bug bounty programs to explore unknown vulnerabilities and bugs to clear
Exploring vulnerabilities using white/black hat hackers and security researchers

Attack Surface Management Service
Attack surface management (ASM) is the continuous discovery, inventory, classification, prioritization or risk scoring, and security monitoring and rating of external digital assets that contain, transmit, or process sensitive data.
Our services in the area include:
Attack surface management against Legacy
Human mistakes and omissions such as phishing and data leaks
Vulnerable and outdated software and Unknown (OSS)
Large-scale and Targeted cyber attacks on your organization
Frequently Asked Questions
Top Skills Required for Cybersecurity?
Problem-Solving Skills.
Technical Aptitude.
Knowledge of Security Across Various Platforms.
Attention to Detail.
Communication Skills.
Fundamental Computer Forensics Skills.
A Desire to Learn.
An Understanding of Hacking.
What are the 5 types of cyber security?
Critical Infrastructure Cybersecurity.
Network Security.
Cloud Security.
Internet of Things Security.
Application Security.
Do you need to be good at math for cyber security?
Many careers in technical fields require the use of math. The quickly growing field of cybersecurity is no exception. Entry-level careers require at least high-school level math and algebra, and highly technical security jobs require even more advanced math.
What are the 3 major types of cyber security?
Application Security. This is the process of protecting sensitive information at the app-level.
Operational Security.
Denial-of-Service Attacks.
Malware.
SQL Injection.
Man-in-the-Middle Attack.
Drive-By Downloads.
Password Attack.
What are 3 cyber domains?
Security and Risk Management.
Asset Security.
Security Engineering.
What is cyber security business?
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security.
Our Clientile
30+ of the world’s most successful companies, big and small, trust NidiTech for their growth





Our Blogs
Stay with our Blogs for know more About the Technology Updates.

Financial Management Automation Bot
Customize your financial management process to fit in exactly the way you wish to operate using Conversational AI.
Read More
Increase your Conversion using our Bots
Increase your conversion rates by 113% by messaging potential customer after making initial contact using our bots.
Read More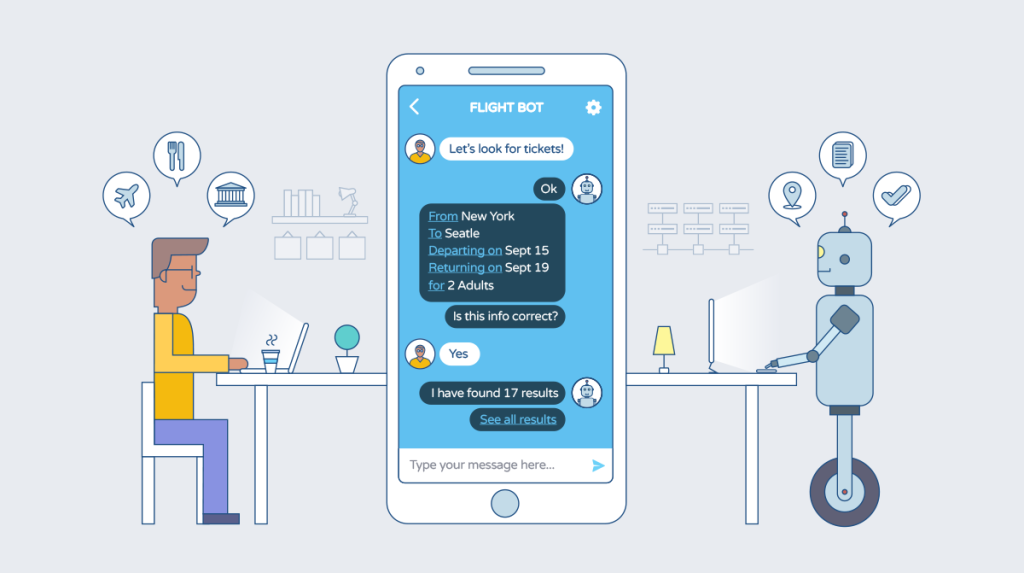
Delivery & E-commerce Platforms Integration
Understanding the data behind online shopping will help you build a strategic plan for your E-Commerce business.
Read More
Increase your Revenue with HYBRID TAP
Keeping track of such messages and replying to them is a high time and resource-consuming task.
Read More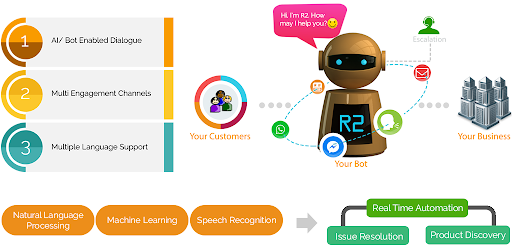
Customer messaging and support using Hybrid Tap
An advanced level of automated conversations with customers and carrying out workflows by tapping
Read More
What is Cognitive Computing?
A co-operative cognitive computing phase between humans and machines, one can call it as the co-computing generation.
Read More
UI?UX Application Modernization
User experience and the user interface is often an area that gets overlooked, as more attention is often focused
Read More
Cloud Computing Business Strategy
size of your organization, small-scale or enterprise, when it comes to cloud computing there are several use
Read More
Observing the Real Potential of Cloud
The way in which technology has evolved, and in particular the rapid advancement in cloud computing capabilities
Read More
Legacy Application Modernization
Legacy application modernization is the process of upgrading or improving your existing platform
Read More