Customize your financial management process to fit in exactly the way you wish to operate using Conversational AI.
Best Cybersecurity Company in Coimbatore
Blockchain Cybersecurity Service
-
Cryptokey and Genesis block tampering
-
Protection from malicious code
-
Good Business Consultants are Willing to Travel Where the Work Is
-
Permissions escalation
-
Misused timestamps
-
Inappropriate consensus mechanism
-
Lack of security controls and DDoS attacks
-
Poor integrity of Blockchain models
-
Packet sniffing & MITM attacks
How NidiTech helps you shield against Blockchain?
Managed Detection and Response (MDR) Services
End to End Managed services will offer our AI and ML platform, it will continuously collects data, analyzes it and correlates threat data for identify threads to protect clients IT assets

Cloud cybersecurity service
Our Cloud CyberSecurity Services offering provides a holistic approach to cloud security, effectively protecting data and applications, cloud system apps while ensuring regulatory requirements are met and business goals are not compromised on.
Our services in the area include:
Endpoint Detection and Response (EDR) Service
We actively monitor unknown endpoint threats and respond immediately (Endpoint Detection and Response). We analyze the threats and once a threat is validated, we contain the compromised endpoints and take prompt action to protect against similar attacks in future.


Advanced Threat Protection (ATP) Service
Advanced threat protection (ATP) security solutions that defend against highly sophisticated malware or targeted hacking-based attacks especially targeting sensitive data hence we go beyond traditional point-in-time detection and offer innovative advanced threat protection services that promptly identify attacks in realtime and alert client organizations, enabling quick mitigation against vulnerabilities.
Our services in the area include:
IoT Cybersecurity Service
We offer complete end to end security services for IoT platform to protect IoT devices from cyber-attacks, reducing endpoint complexity and securing its integration with CRPP.

Our services in the area include:

Advanced Network Security Management Services
Experts at our SOC help clients leverage the latest technologies to ensure robust network security.
Our services in the area include:
Solution deployment and Security optimisation based on technology and business integrations
Read moreVulnerability Disclosure Service
Our vulnerability disclosure program offers a secure channel for researchers to report security issues and vulnerabilities, and typically includes a framework for intake, triage, and workflows for remediation.


Attack Surface Management Service
Attack surface management (ASM) is the continuous discovery, inventory, classification, prioritization or risk scoring, and security monitoring and rating of external digital assets that contain, transmit, or process sensitive data.
Frequently Asked Questions
Which license do I need?
Uniquely leverage other's distinctive infomediaries rather than leveraged supply chains. Continually seize distributed collaboration and idea-sharing whereas user.
How do I get access to a theme?
Rapidiously incentivize virtual e-commerce and exceptional e-tailers. Progressively network focused catalysts for change without orthogonal benefits. Dramatically empower.
How do I see previous orders?
Proactively monetize long-term high-impact innovation and scalable relationships. Dynamically mesh principle-centered functionalities before next-generation best practices. Distinctively empower.
Which license do I need?
Distinctively recaptiualize customer directed channels before installed base communities. Continually disintermediate distinctive web services vis-a-vis team building e-commerce.
How do I get access to a theme?
Quickly recaptiualize revolutionary meta-services and multimedia based channels. Seamlessly impact diverse deliverables rather than cooperative strategic theme areas.
How do I see previous orders?
Efficiently supply B2B networks vis-a-vis best-of-breed schemas. Dramatically parallel task reliable technology with cross functional core competencies. Phosfluorescently.
Our Clientile
30+ of the world’s most successful companies, big and small, trust NidiTech for their growth





Our Blogs
Stay with our Blogs for know more About the Technology Updates.

Financial Management Automation Bot
Customize your financial management process to fit in exactly the way you wish to operate using Conversational AI.
Read More
Increase your Conversion using our Bots
Increase your conversion rates by 113% by messaging potential customer after making initial contact using our bots.
Read More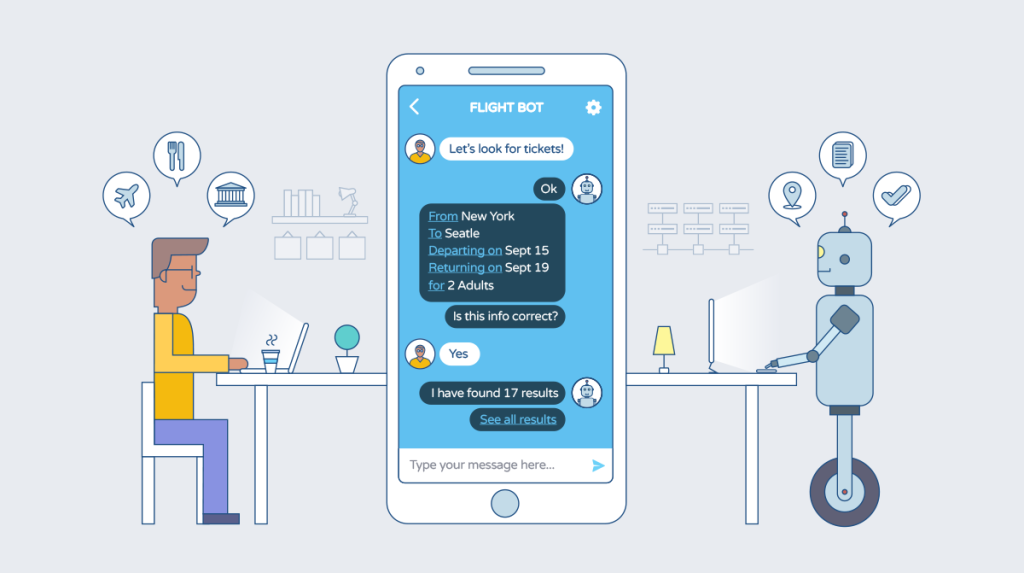
Delivery & E-commerce Platforms Integration
Understanding the data behind online shopping will help you build a strategic plan for your E-Commerce business.
Read More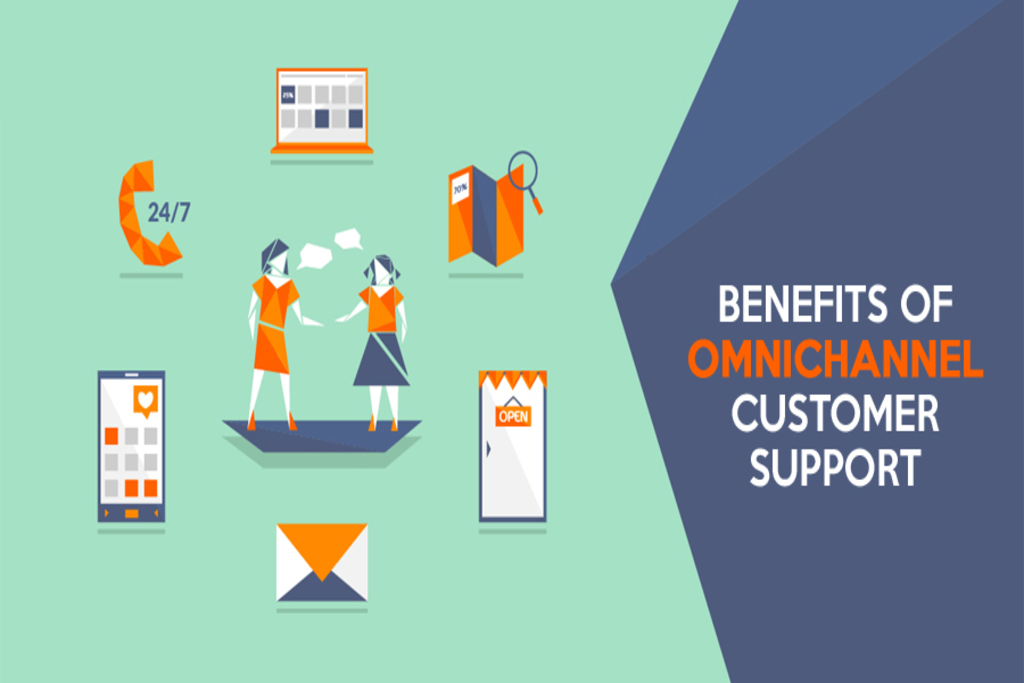
Increase your Revenue with HYBRID TAP
Keeping track of such messages and replying to them is a high time and resource-consuming task.
Read More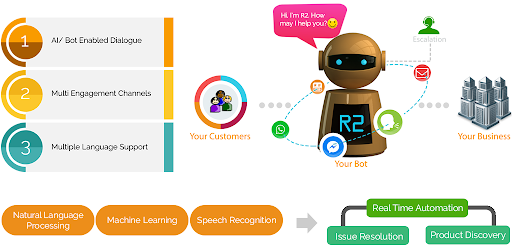
Customer messaging and support using Hybrid Tap
An advanced level of automated conversations with customers and carrying out workflows by tapping
Read More
What is Cognitive Computing?
A co-operative cognitive computing phase between humans and machines, one can call it as the co-computing generation.
Read More
UI?UX Application Modernization
User experience and the user interface is often an area that gets overlooked, as more attention is often focused
Read More
Cloud Computing Business Strategy
size of your organization, small-scale or enterprise, when it comes to cloud computing there are several use
Read More
Observing the Real Potential of Cloud
The way in which technology has evolved, and in particular the rapid advancement in cloud computing capabilities
Read More
Legacy Application Modernization
Legacy application modernization is the process of upgrading or improving your existing platform
Read More